
blackhatrussia0x0
-
Content Count
119 -
Last visited
Posts posted by blackhatrussia0x0
-
-
let me try it check it and reply it
-
wow what a huge features
-
-
highly recomnded tools for all
-
wow nice package
-
looks very good tools i am going to download
-
looks very nice brother
-

[align=center]Learning Tor and the Dark Web
MP4 | Video: AVC 1280x720 | Audio: AAC 48 kHz 2ch | Duration: 1 Hour | 132.3 MB
Genre: eLearning | Language: English
[/align]
==========
[align=center]
[video=youtube]https://www.youtube.com/watch?v=2wdwdh1SlGU
The dark web-a bastion of encrypted websites that can be visited and hosted anonymously-is home to criminals and privacy-minded citizens alike. In this course, learn about the social and technical underpinnings of the dark web, as well as how you can access and host websites that are hidden from prying eyes. Instructor Mike Chapple provides some history on the dark web and the Tor Browser, the basic software needed to access the dark web and browse the internet anonymously.
He then goes over the basics of encryption and shines a light on the technical aspects of the Tor network, as well as how to use it to browse the standard Internet anonymously. Plus, get briefed on the potential vulnerabilities that users of anonymized networks should watch out for.
ICQ:653580170
jabber: [email protected]
[hide]
[/hide]
[/align]
-

[align=center]Kali Linux - Complete Training Program from Scratch
Lectures: 120 Video: 19 Hours Skill level: All level Languages: English Course Description
[/align]
==========
[align=center]
[video=youtube]https://www.youtube.com/watch?v=zBv_IaOWWbw

Kali Linux is specifically tailored to the needs of penetration testing professionals. Kali Linux is a Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing. Kali contains several hundred tools aimed at various information security tasks, such as Penetration Testing, Forensics and Reverse Engineering. Kali Linux is developed, funded and maintained by Offensive Security.
Kali Linux will prepare you to enter the world of professional hacking by ensuring that you are well versed with the skills needed and tools used to compromise the security of enterprise networks and information systems. It is no longer sufficient to merely rely on traditional security measures. In order to ensure the security of critical information assets, it is essential to become familiar with the strategies, tactics, and techniques that are used by actual hackers who seek to compromise your network.
What are the requirements?
Basic understanding of Linux
A PC with internet
TCP/IP will be helpful
What am I going to get from this course?
Over 120 lectures and 18 hours of content!
Learn Kali Linux in details starting from scratch
Analyze Cross-Site Request Forgery attacks to defend your system against them
Safeguard user credentials by figuring out how Bruteforcing works
Many advanced techniques are addressed
What is the target audience?
Anybody interested in information security, penetration testing or ethical hacking
Web Developers
Linux users
IT Professionals
ICQ:653580170
jabber: [email protected]
[hide]
[/hide]
[/align]
Kali Linux,Kali Linux Training,kali linux tutorial,how to use kali linux,kali linux complete hacking tutorial,kali linux free tutorial,kali linux course,penetration testing training with kali linux,kali linux guide,penetration testing with kali linux training course,
-
 1
1
-
-

[align=center]The Complete Wireshark Course 2019
Video Details
English | Size: 1.43 GB | Genre: eLearning
[/align]
==========
[align=center]
During this Wireshark Course you will learn about the Wireshark Interface, its available menus and how to use this amazing application with ease. You will also learn some basic information about networking, the various layers and protocols used for todays networks allowing you to understand the information found within Wireshark but also to ensure that the basics needed to use Wireshark are covered. Later in the Course some examples of Wireshark capture will be reviewed as well an overview of the included applications that come bundled with Wireshar
What is learned:
Introduction & Use Of Wireshark
Network Analysis and Sniffing
Network understanding
Network Protocols
Protocol disassembly
Network Devices
Wireshark Installation
Wireshark Interface
Using Wireshark
Wireshark Optimization
Wireshark Menu
Wireshark Capture
Wireshark Analysis
Wireshark Statistics
Wireshark Tricks
Capturing Traffic
Real World Captures
Supporting Tools
ICQ:653580170
jabber: [email protected]
[hide]
[/hide]
[/align]
Wireshark Course 2019,wireshark course,wireshark training,network security,monitoring tools,network sniffer,learn wireshark,packet sniffer,wireshark online training
-

[align=center]EC Council Certified Ethical Hacker CEH 9
Ethical Hacker Certification or Certified Ethical Hacker?
[/align]
==========
[align=center]

Ethical Hacker Certification or Certified Ethical Hacker (CEH) originally Security experts familiar with the methods, techniques and tools used by hackers is.
Providers believe that this period should have to fight through expensive methods they use familiar tools and the mindset of hackers was aware.
With this view, a security expert can network your desired as an attacker, test, troubleshoot and provide safer. At the end of the course students should be able to recognize a variety of attacks and attack tools and methods to identify and block network intrusion and computer systems. Who has just come out of eight it by the Council.
In the present set of books periodic hacking CEH 9 for direct contact law degree course has been collected.
ICQ:653580170
jabber: [email protected]
[hide]
[/hide]
[/align]
EC Council Certified Ethical Hacker CEH 9,EC Council Certified Ethical Hacker CEH ,EC Council Certified Ethical Hacker,Certified Ethical Hacker,ethical hacking,ethical hacking course,ceh certification,ethical hacking certification,ethical hacking online course,ethical hacking training,certified ethical hacker training
-

[align=center]ITPro – ECIH EC-Council Certified Incident Handler
English | Size: 4.5 GB | Genre: eLearning
[/align]
==========
[align=center]
This course covers the exam objectives of EC-Council’s Certified Incident Handler (ECIH) program. It discusses the basic skills to handle and respond to security events and addresses various underlying principles and techniques for detecting and responding to current and emerging computer security threats.
ICQ:653580170
jabber: [email protected]
[hide]
[/hide]
[/align]
Certified Incident Handler,ITPro – ECIH EC-Council Certified Incident Handler,ECIH EC-Council Certified Incident Handler,EC-Council Certified Incident Handler,cissp training,security plus certification,certified information systems security professional,cisco ccna certification,incident response certification
-

[align=center]EC-Council – Computer Hacking Forensic Investigator (CHFIv9)
English | Size: 23.56 GB | Genre: eLearning
[/align]
==========
[align=center]

EC-Council Computer Hacking Forensic Investigator (CHFIv9) Complete Course including Instructor Materials
Courseware
Lab Manuals
Instructor Slides
CEI Briefing
Tools
Exam Dump
ICQ:653580170
jabber: [email protected]
[hide]
[/hide]
[/align]
computer hacking forensic investigator,computer hacking forensic,computer hacking course,hacking training,ceh training,ceh exam,ethical hacking certification,certified ethical hacker training,certified ethical hacker exam,ceh course,chfi training
-
wow what a leak keep it up
-
wow what a huge collection nice
-
its virus or proxy grabber any one tested it
-

[align=center]Hacking Android
very usefull book for starting hacker with full tools and tutorials
[/align]
==========
[align=center]
Chapter 1:Setting up the Lab
Chapter 2:Android Rooting
Chapter 3:Fundamental Building Blocks of android apps
Chapter 4:Overview of Attacking Android Apps
Chapter 5:Data Storage And its Security
Chapter 6:Server Side Attacks
Chapter 7:Client Side Attack Static Analysis Techniques
Chapter 8:Client Side Attack Dynamic Analysis Techniques
Chapter 9:Android Malware
Chapter10:Attacks on Android Devices
ICQ:653580170
jabber: [email protected]
[hide]
[/hide]
[/align]
-
wow what a huge leakds
-
wow nice leak dear
-

[align=center]AndroRAT - AndroBinder+Tutorial
AndroRat is RAT for smartphones on Android. Written in Java, the following functions are supported:
[/align]
[video=youtube]https://www.youtube.com/watch?v=ckIKgxvHYoM&t=1s

Get a list of contacts and all information about them;
Get call logs;
Get all messages;
Get the current location by GPS;
Monitoring incoming messages in real time;
Monitoring the status of the phone in real time (incoming calls, missed calls, etc.);
Capture images from the camera;
Streaming sound from a microphone (or from another source);
Streaming video from the camera;
Send an SMS message;
Make a call;
Open the URL in a standard browser;
Make the phone vibrate.
ICQ:653580170
jabber: [email protected]
[hide]
[/hide]
-

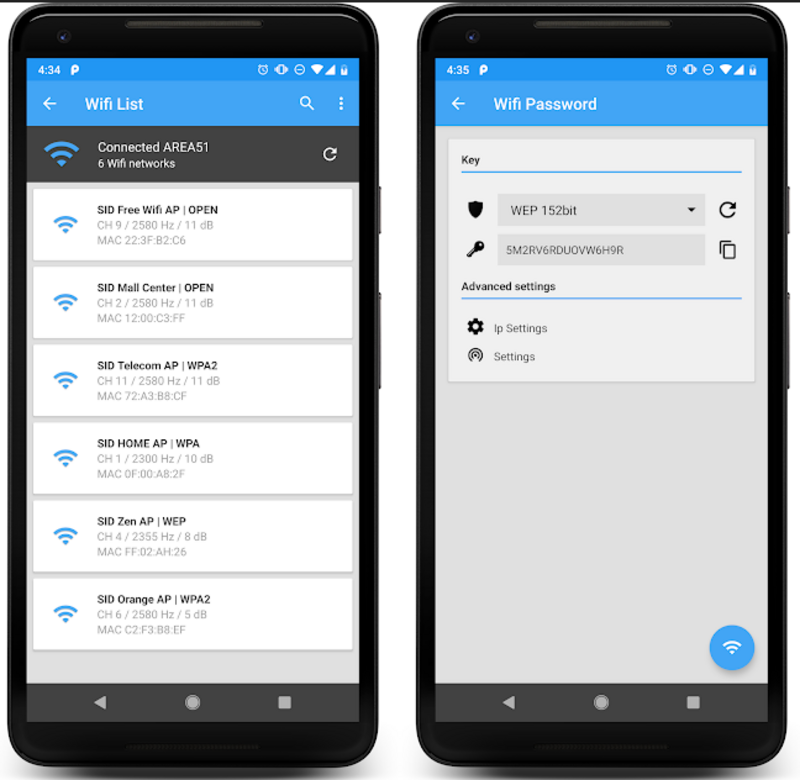
[align=center]WIFI PASSWORD PRO v5.6.0 (Unlocked)
Wifi password pro generate a long random alphanumeric password to provide you a better security in your wifi network.
[/align]
==========
[align=center]
This app will not hack steal or retrieve wifi network password it's just a security tool to help you increase your security generating long random passwords that you have to set it manually to your wifi router.
Features
• The algorithm generate WEP WPA WPA2 with a high level of authentication.
• Direct connection to wifi networks without password.
• Order network list by proximity open sid mac security channel and frequency.
• Multi search.
Optimized for mobiles and tablets.
Compatible with Android 6.0 and more.
ICQ:653580170
jabber: [email protected]
[hide]
[/hide]
[/align]
how to hack wifi login,how to hack wifi password,how to hack wifi,wifi hacker,wifi password hacker,how to get wifi password,hack password wifi,wifi cracker,how to unlock wifi password,wifi password finder,hack wifi password android,how can i hack wifi password
-
looks nice dear link still up vouch for you
-

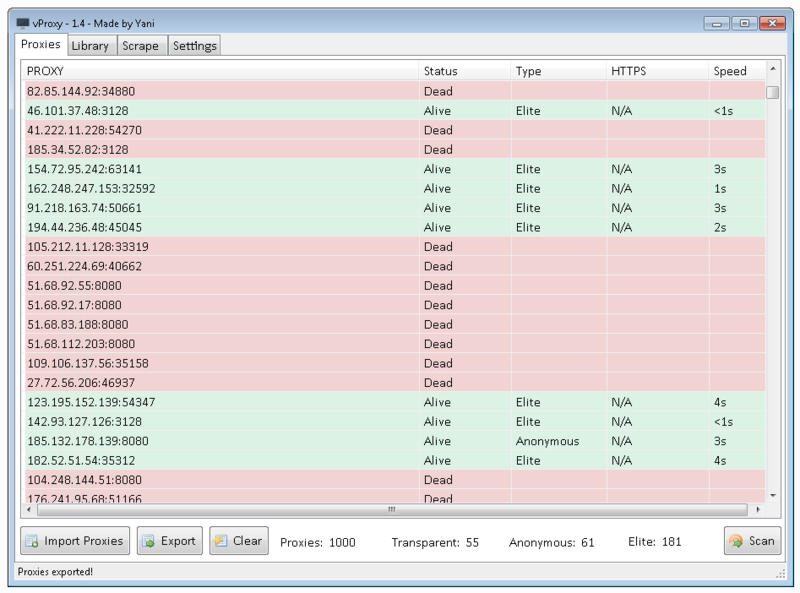
[align=center]vProxy v1.4
Simple and clean Proxy Suite that offers you everything you need for getting fresh proxies.
It’s written in .NET 4.5 and is meant to be as simple as can be.
[/align]
==========
[align=center]
https://www.youtube.com/watch?v=Qjv2HK258Ms&feature=youtu.be
Features:
Scanner & Scraper
Built-in library system
Fast and accurate
Very easy to use GUI
Multi-threaded
HTTP Filter (Transparent/Anonymous/Elite)
Latency report
Built upon the .NET 4.5 Framework
Comes with 500+ proxy scraping sources
ICQ:653580170
jabber: [email protected]
[hide]
[/hide]
[/align]
proxy grabber,proxy scanner,proxy scraper,proxy checker,socks checker,online proxy checker,scraper tool,ip proxy checker,working proxy list,private proxy,vpn proxy,test proxy server,
-
let me try it hope link still up










FREE BTC MINER
in Cracked Programs
Posted
i am searching for it got it finaly